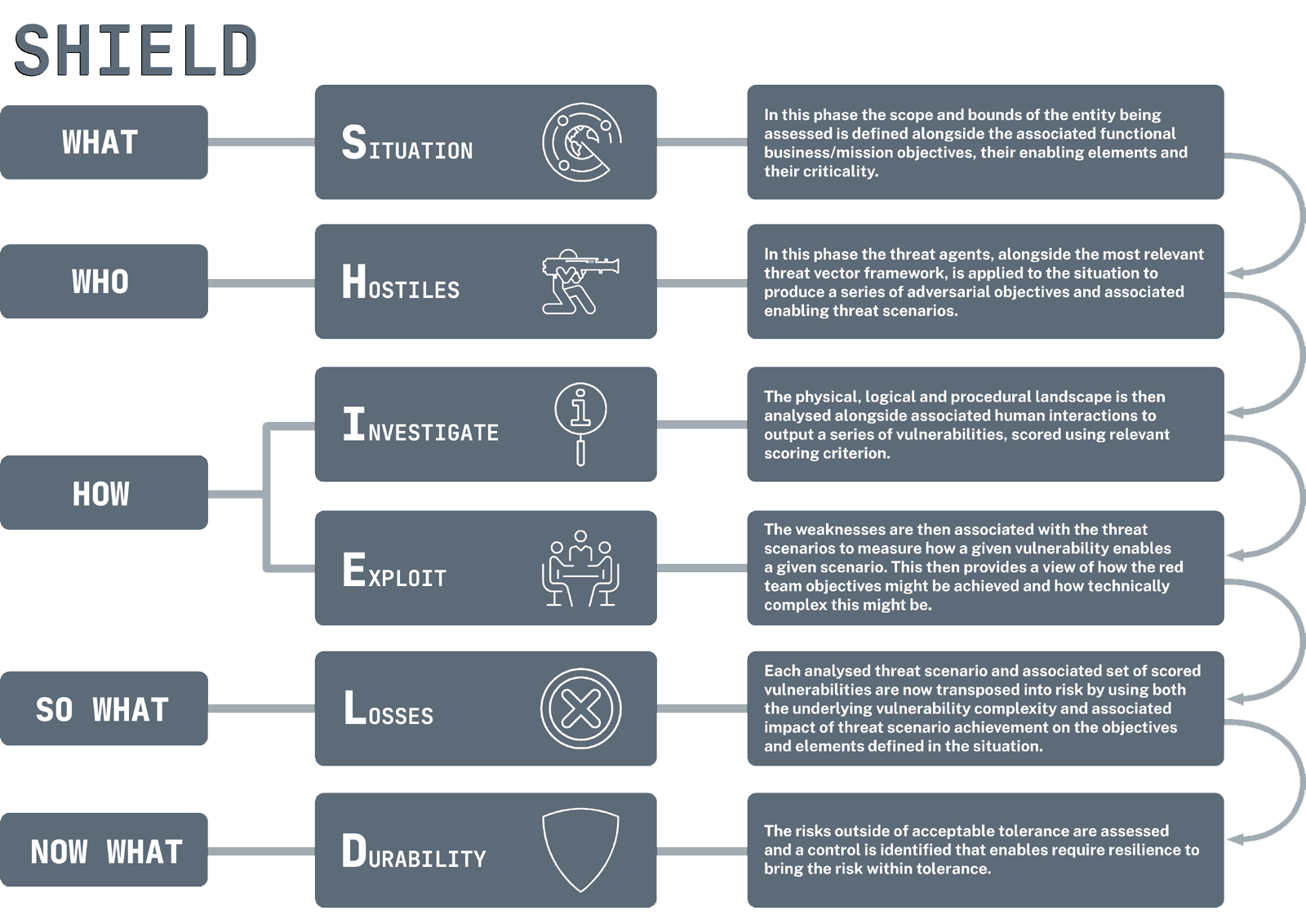
Leonardo is certified by UK HMG through the UK NCSC in delivery of guidance around cyber security risk management, and is an established leader in identification and analysis of cyber risk in complex technological environments. Leveraging this experience, Leonardo has designed the 6-stage S.H.I.E.L.D risk assessment methodology. S.H.I.E.L.D is a threat-centric, mission-informed way to identify, analyse, evaluate and respond to cyber risks. It follows a logical flow of stages: Situation, Hostiles, Investigate, Exploit, Losses and Durability.
The modular stages of S.H.I.E.L.D align with international best practices, achieving the outcomes and stages of risk assessments defined in ISO-31000 and ISO27005, alongside the risk assessment process defined in NIST CP-800-30. The modular stage-based design of S.H.I.E.L.D enables the creation of bespoke mission-centric risk measurement criteria or the adoption of established organisational risk measurement criteria.
S.H.I.E.L.D Risk Assessment: identification, analysis and evaluation of the security risks attracted by a given change, mission and / or platform across cyber, physical and socio technical.
Expert advice and guidance on appropriate risk response options help inform and guide operational security risk management from a UK NCSC-certified cyber risk management consultancy.
The Leonardo S.H.I.E.L.D provides risk assessors with a consistent and modular way to identify, evaluate and characterise the cyber risk a solution attracts in high threat scenarios, as well as ensure maximum security return on investment for any security and resilience controls needed to manage associated risk to within acceptable levels and gain confidence in mission success.
Some key ways in which S.H.I.E.L.D helps are:
- Establishing functional target objectives at the start of the assessment to ensure appropriate context prior to and not after system threat profiling.
- Using mission context to link threat agents to associated red-team objectives to build realistic and mission centric threat scenarios.
- Building threat scenarios using modular threat vector frameworks such as (but not limited to) MITRE ATT&CK, MITRE ICS, MITRE SPARTA, NSA CTTF.
- Enabling people, process and technology weaknesses to be considered in unison, using a modular scoring system and centralised threat scenario.
- Transposition of threats to risks using mission-centric measurement criteria that can be inserted into the method or self-defined.
Benefits
- Risk-based approach to security investment, allowing informed choices about when to accept, reduce or avoid security risks.
- Clear characterisation of risk and its impact on the underlying mission to allow for more targeted use of controls to achieve resilience.
- Organisationally-aligned risk analysis in line with industry best practice and most UK cyber regulatory baselines.
A high level of the S.H.I.E.L.D methodology is shown below.